Privacy and Security
These days much of our information is online. It is important to keep that information private and secure. Navigating cyberspace presents other problems as well, such as scams and identity theft. Below find key tips for keeping yourself and your data secure.
Stronger passwords are required to help protect your identity. Here is a list of 10 Dos and Donts for Powerful Passwords.
Use Multi-Factor Authentication (MFA) where possible This process requires the presentation of at least two independent authentication factors. The first is a knowledge factor. It is something only the user knows, which is usually a password. The second piece of information comes from something the user possesses, e.g., a text message sent by the site to your phone. It is important to add MFA to all possible accounts because even if someone knows or guesses your password, they will not be able to access your account without the randomly generated second factor that must be presented for identification. Many big sites, including Facebook, Google, Microsoft, and Apple, offer MFA for your protection.
Carefully select what and when you share information Be careful to not share your full name, address, and account numbers. Any messages in cyberspace that request you to share private information are immediate signs that you might be facing a scam artist. If a scam is suspected, do not reply or click on links.
There is more spam sent daily than there are people living on the earth; some 10 billion spam emails are sent. A significant amount of this junk email is nefarious. Internet junk mail should never be opened and immediately deleted. If you cant identify the mail, its probably not worth opening. Even if you can identify the sender, open an email with caution, and never click on links in these emails. To prevent your operating system from becoming compromised, manually enter the URL into the browser. Links that appear to be correct may, in fact, point to a different URL.
See the example from Microsoft's phishing page next.
Phishing scams are common both on and offline. According to Microsoft, phishing is a type of scam that can come through email messages, websites, and phone calls. They are designed to steel your information, identity or money. Cybercriminals can do this by installing malicious software on your computer or stealing personal information off of your computer. The Securities and Exchange Commission provides useful advice for avoiding many of the phishing scams that you might run into. MORE INFORMATION HERE
- Slow down Spammers want you to act first and think later.
- Research the facts Be suspicious of any unsolicited messages.
- Delete any request for financial information or passwords. If you get asked to reply to a message with personal information, its a scam.
- Reject requests for help or offers of help Legitimate companies and organizations do not contact you to provide help.
- Don't let a link be in control of where you land Stay in control by finding the website yourself using a search engine to be sure you land where you intend to land.
Once something is posted or transmitted, there is a permanent record of it. Even with programs that claim to delete content such as Snapchat or Wickr, content is recoverable. Moreover, other users can take screenshots of the content. Be thoughtful in what you post online as it will be with you forever and may have devastatingly negative consequences.
All social networks have different terms of service (TOS) and privacy settings. Learn about privacy settings and set yours to protect your family online. Most importantly, never say or do anything online that you wouldn't say or do in front of your parents or guardians.
- Do make passwords eight or more characters long. (Longer passwords are harder to crack than shorter ones.)
- Don't use dictionary words as your password. (Others could guess your password this way.)
- Do include letters, numbers, and symbols in your password. (It can be harder to guess passwords with this combination.)
- Do change your password at least every six months. (This way, even if someone does guess your password, they won't be able to get into your account for long.)
- Don't use private identity information in your password. (Others could guess your password this way.) Never use any of the following in your password:
- Full (first and last) name
- Date of birth
- Mother's maiden name, Dad's middle name, etc.
- Street address
- School name or school address
- Credit card numbers
- Phone numbers
- Social Security number
6. Don't use your phone number as your password. (Others could guess your password this way.)
7. Don't use your nickname as your password. (It could be easy for others to guess.)
8. Do give your password to your parent or guardian. (They will help you remember it if you forget it.)
9. Don't share your password with your friends. (Even if you trust them, they might unintentionally do something that puts you or your information at risk.)
10. Do create a password that you can remember. (Its okay to create a random password, but keep in mind that it should be one that you can remember, or else it wont do you much good.)
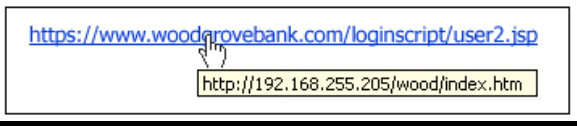
In the picture, notice that while the blue link says Wood Grove Bank, the true URL is pointed to 192.168.225.205/wood/index.htm.
Today, general scams that are sent to everyone are giving way to Social Engineering scams. Webroot defines Social Engineering as the art of manipulating people so they give up confidential information. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious software that will give them access to your passwords and bank information as well as giving them control over your computer. Visit the Webroot site to see the most common scams and how to protect yourself from them.
Some examples include:
- Messages that respond to a question you never had.
- Messages asking for help or stating that you are a winner.
- Messages that looks like they are from a friend of yours.
- Messages containing links or downloads.
- Make sure that your child takes advantage of the privacy settings on social networking sites.
- Pre-approve the pictures and videos your child posts online.
- Remind your child never to post e-mail addresses or cell phone numbers.
- Tell your child that passwords should only be shared with parents and guardians.
- Teach your child not to respond to any e-mails requesting personal information and to delete e-mails from unknown senders.
- Discuss how to keep screen names and e-mail addresses gender-neutral, appropriate, and free of any information that could reveal identity.
- Encourage your child to tell you right away if anything happens online that bothers or frightens him or her.
Advise students that companies and websites collect data and utilize collected data to personalize content for their users. While this can be incredibly useful for maintaining a personalized online experience, it is also a privacy concern. Know the TOS for the sites you use. Understand that nothing is free. Sites that offer services for free do so by monetizing your personal data. Google provides incredible services that many of us cannot do without, however, they fund these services with your personal information. Other sites have similar business models. These models are perfectly acceptable; just understand what you are giving up for those services.